
You may recall a recent uproar on social media, shortly after Independence Day, when the google.lk domain appeared to have been defaced, redirecting users to a site that detailed ongoing social issues. At first, it seemed like the typical website defacement that has been known to take place around important dates on the Sri Lankan calendar (not that this is something to be relieved about). Upon digging further, however, the situation appeared to be more dire than initially suspected.
What Happened?
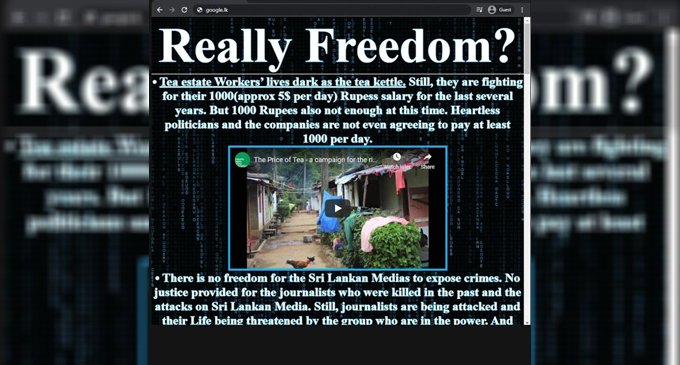
On 6 February, many users’ traffic to google.lk redirected to a propaganda page in what seemed to be the work of hacktivists. The page drew attention to several contemporary national issues, including struggles faced by plantation workers and the Tamil community, as well as the issues of Tamil political prisoners and ‘forced cremations’ of COVID-19 victims. The incident first made the rounds on social media following a tweet by Groundviews founder Sanjana Hattotuwa. This was followed by notices from several tech bodies, including the LK Domain Registry. This is Sri Lanka’s country code top-level domain registry for .lk. It’s an independent non-profit organisation based at the University of Moratuwa, and has been operating since 1990.
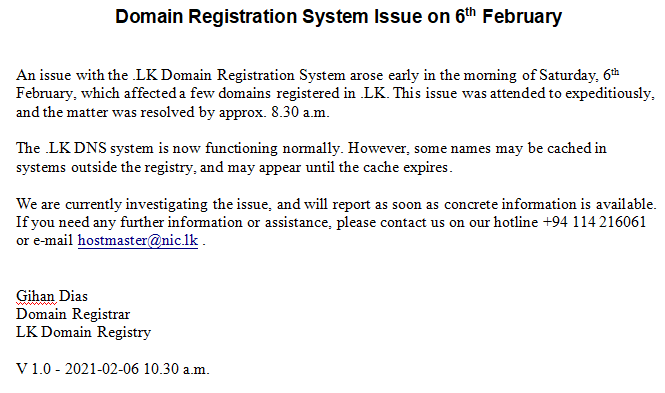
A few hours in, the google.lk redirect appeared to have been fixed. However, according to cyber security specialist, Asela Waidyalankara, authorities at this point were already looking into possible breaches to other .lk domains.
https://twitter.com/aselawaid/status/1357933056275984386
Meanwhile, Professor Gihan Dias, LK Domain Registry’s Domain Registrar, said that about 10 domains were affected by the malicious redirect. He explained that they were “looking at the weaknesses and identifying them”, and that the domain registry will ensure the incident won’t be repeated.
Meanwhile, a breakdown by Twitter user Duminda (@dumindaxsb) revealed attempts by one IP address at impersonating the HSBC Sri Lanka website in a similar fashion.
He also discovered that a malicious file was served on google.lk to Windows machines during the 6 February incident. Duminda speculates that this could be an Internet Explorer (IE) exploit. There are many government and corporate offices that continue to use IE. This means that the exploit could potentially impact thousands of computers in the island. Duminda further notes that if you’ve visited google.lk or another compromised site and downloaded/accessed a file, it’s best you format your computer immediately. This is regardless of what browser you’ve used.
How Did The Attack Happen?
The attack itself was made possible via a method called DNS cache poisoning (also known as DNS spoofing). This is where false information is entered into a DNS cache, which returns an incorrect response and users are redirected to the fraudulent websites. The repercussions of such an attack can range from users inadvertently submitting login information to malicious parties, to user computers being infected with malware.
Although the 6 February incident was initially considered an isolated attack, what we have learnt since then raises reasons for concern.
Reporting from Cyber Security Works indicates that nic.lk domain usernames and their passwords have already been exposed in the dark web. To make matters worse, it turns out that these admin username and password combinations have been used in multiple websites since 2012. That’s eight years of using the same credentials.
What this means is that though we seem to have fended off one attack, another is very likely — particularly considering how any malicious users could simply use the exposed details on the dark web.
How We Can Prevent Recurrence
Almost a week after the attack, LK Domain Registry issued a statement regarding the incident. Addressing the impact of the attack, the statement reads, “There is no evidence of any other unauthorised access to our systems. We have also not found any evidence of changes to any .lk websites, or of any information being stolen from any other .lk websites. We have not found any substantial evidence that any malware had been distributed via the website pointed to by the attackers.”
Commenting on the security lapses, the statement further mentions, “Together with TechCERT, we have identified shortcomings in our security mechanisms, and have updated our systems to mitigate these vulnerabilities. A number of other security improvements have also been implemented.”
But questions remain as to how far this breach goes; if @dumindaxsb’s findings are any indication, the issue is more serious than a mere malicious redirect. In other words, this won’t be the last time Sri Lanka could face a cyber attack of this magnitude.
But what can authorities really do to prevent such incidents from taking place?
The first step would be to recognise that we as a country have neglected cybersecurity for a long time. Time and time again, we have seen authoritative bodies disregard security when it comes to digital solutions. A good recent example is the Stay Safe project.
Recognising the problem is only half of the solution. The other half requires a proactive approach towards security instead of a reactive one ― particularly in a landscape where digitalisation is actively being promoted at a national level. But the fact that the same domain credentials for nic.lk, Sri Lanka’s top-level country code domain provider, has been in use for eight years, reflects the severity of flaws in our cybersecurity approach.
Then there is the matter of communication ― or rather, the lack of it.
Throughout the breach, communication from official channels were lacklustre. This is not ideal, considering that national-level IT infrastructure was compromised and citizens were left in the dark about what was happening. An important element of being proactive has to do with upfront communication with all relevant stakeholders.
All of this tells the story of the worrying state of our country’s cybersecurity — which in turn begs the question: are we really ready for a digital Sri Lanka?


